Operational Plan
Our team of experts will guide you through a battle-tested plan—built and refined over 15 years and across the world’s most complex IT environments.
Enable
Let Varonis start uncovering key risk insights, automatically.
-
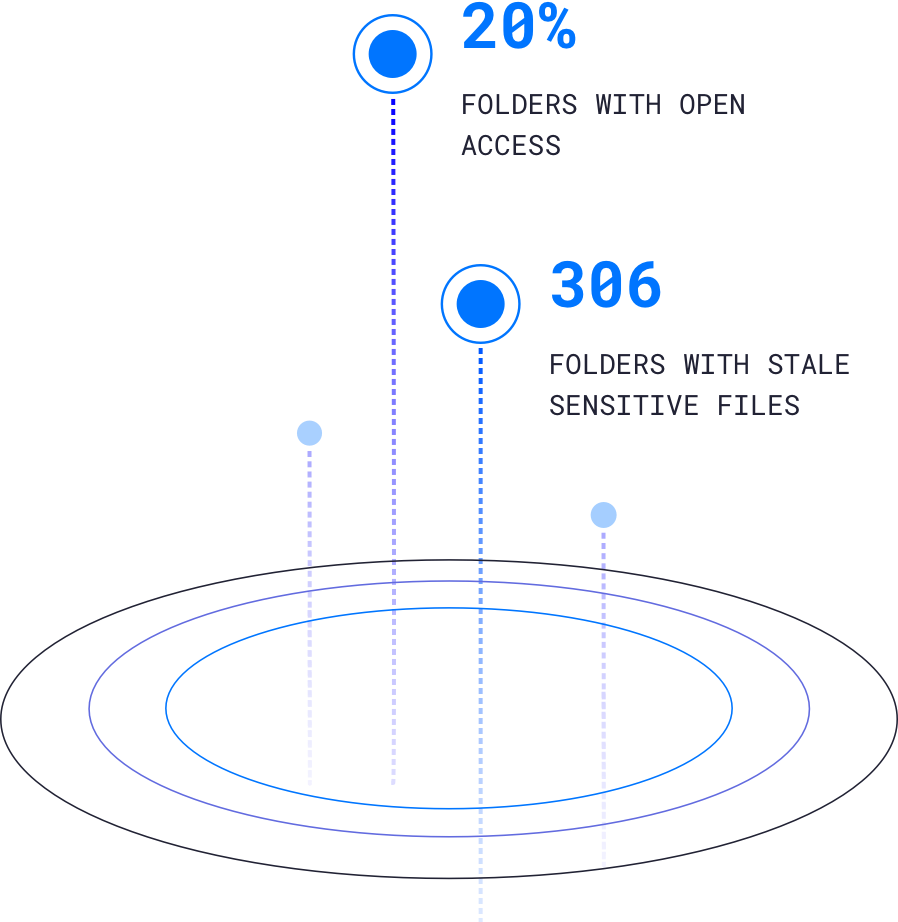
Map all data and resource entitlements
-
Automatically classify sensitive data
-
Baseline user, device, and data activity
-
Evaluate & prioritize risk
-
Start regular business value reviews
Learn & Tune
The Varonis AI learns your environment and our teams help you finetune and customize.
-
Tailor dashboards and automate reporting
-
Tune UBA alerts with the Varonis Incident Response Team
-
Integrate with SIEM, SOAR, DLP, IAM, ITSM and other technologies
-
Index data & automate DSAR process
No-cost incident response help
Our expert incident responders help you with investigations free of charge.

Remediate
Use automation to self-heal the risks that humans invariably introduce.
-
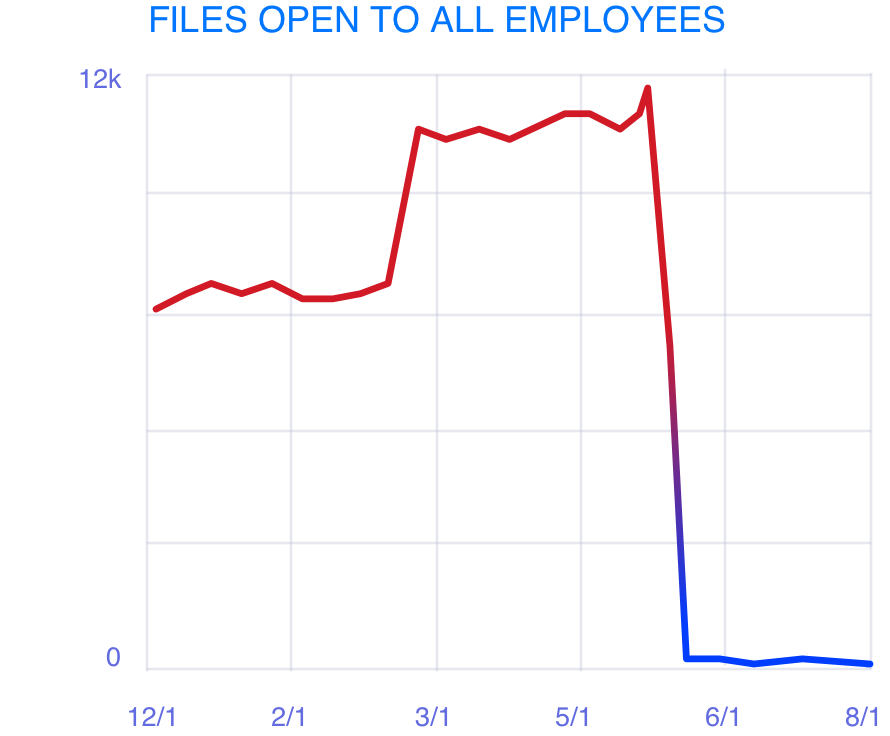
Automatically reduce your blast radius
-
Harden your Active Directory
-
Automate data retention & quarantining policies
-
Remove stale permissions
Align
Prevent data exposure by putting data owners in charge of their data.
-
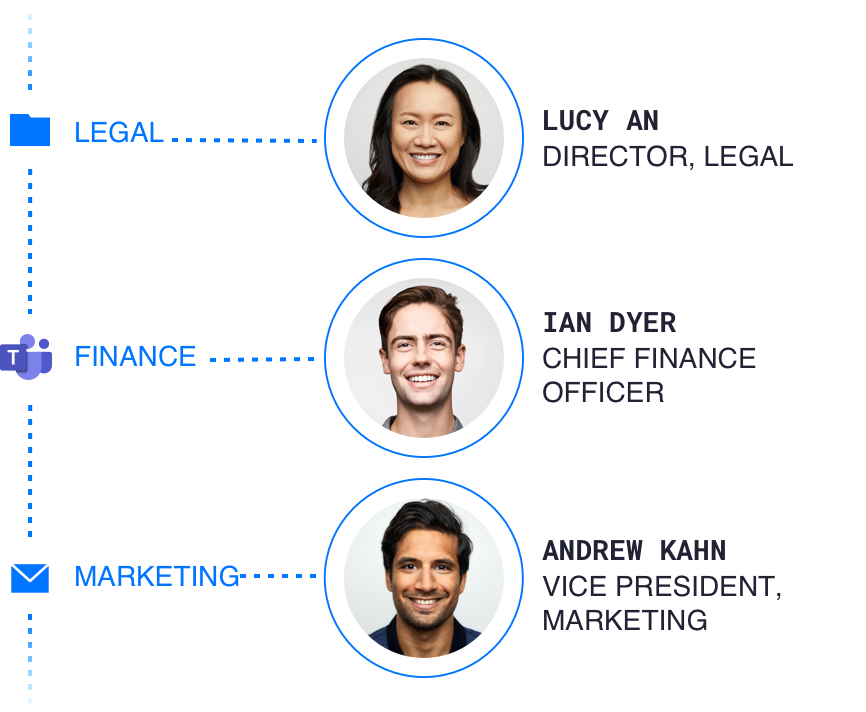
Identify and assign data owners
-
Implement data owner self-service
-
Automate entitlement reviews
Real results:
Ensuring your success
Partner with your Varonis team to maximize your investment and risk reduction.
-
Regularly review risk indicators, business value, and security maturity
-
Leverage free product training—both live and on-demand
-
Enable Live Updates to get new product features and bug fixes without having to upgrade

Varonis’ support is the best support of any software solution that I have worked with. They’re always there to help at no additional cost.
Reduce your risk without taking any.
Get a free, true-to-life report based on your company data, that reveals the vulnerabilities and exposures hackers hunt for.