Malware is simply a piece of code that attempts to hide and perform a predetermined set of actions to gain access to sensitive data or cause disruption in the operations of the originating computer — malware protection quite simply aims to deter malware attacks. It’s a term that has been overused by most in a broad-brush attempt to sell end users on some form of security. At a corporate level, malware can threaten the current state of your security by advertently performing actions that are against security policy, thus threatening the integrity of your sensitive documents or information.
Nowadays, with the interconnectedness of personal and commercial systems, bring your own device and work from home it is common to discover cases where individual malware infection has spread to the larger corporate network. It is crucial to the overall integrity of your company to have a clear understanding of what malicious software looks like and what types of malware protection you can instill into your security posture to protect your physical and digital assets better.
Want to learn ransomware basics and earn a CPE credit? Try our free course.
Whether it is something as simple as a phishing email that contains a bot to harvest bitcoin or a more complex malware like a trojan that is attempting to install a direct backdoor into your enterprise infrastructure. It is vital that you know which controls to have in place to accurately detect and remediate each situation promptly.
To learn more about the basics and earn a CPE credit, unlock this free intro to ransomware course, led by Troy Hunt.
How Does Malware Work?
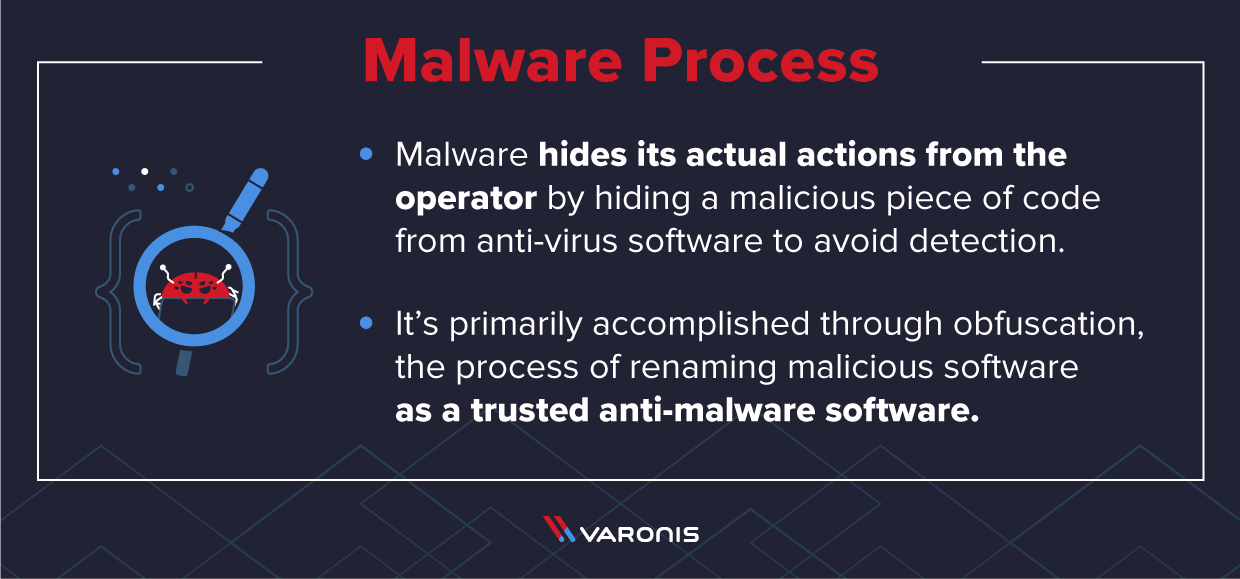
Malware operates using several methods to ultimately hide its actual actions from the operator. The most common way malware software operates is by hiding a malicious piece of code from the anti-virus software to avoid detection. The primary way this is accomplished is through obfuscation.
Obfuscation
Obfuscation involves renaming a malicious software the same name as a trusted anti-malware software. Here are the basics of how it works:
- Malware is contracted to the end-users machine via phishing
- It installs itself as a legitimate piece of software at face value
- The underlying code opens up a route on the machine’s local firewall
- This allows all traffic through a similar port of the intimidated file to hide from the local anti-virus software.
All this takes place within seconds after the end-user opens the malicious software that was sent over in the phishing email received.
Disguised Functionality, Or Malware that Isn’t Malware
Then there is malware that isn’t actually malware, but it’s a legitimate application that behaves like malware. For example, the legitimate file found in HP laptops, the Mictray64.exe, or “fileless malware,” which is where attackers live off the land and use the applications on your computer in the attack.
The sole purpose of the MicTray64.exe is to help gather keystroke data and send it back to HP for troubleshooting (if permitted). Most organizations do not use the local HP debugging as a reliable method for troubleshooting issues, so this feature is disabled by default upon installation.
Unfortunately, most organizations also wouldn’t know if that feature was reenabled ether. Hackers can reenable the MicTray64.exe, change the write location of the troubleshooting to one that they have access to, and thus capture all keyboard strokes made on the computer moving forward.
This is an excellent example of how a legitimate file can be used against a user, while also bypassing the local malware anti-virus software.
Steps in a Typical Malware Attack
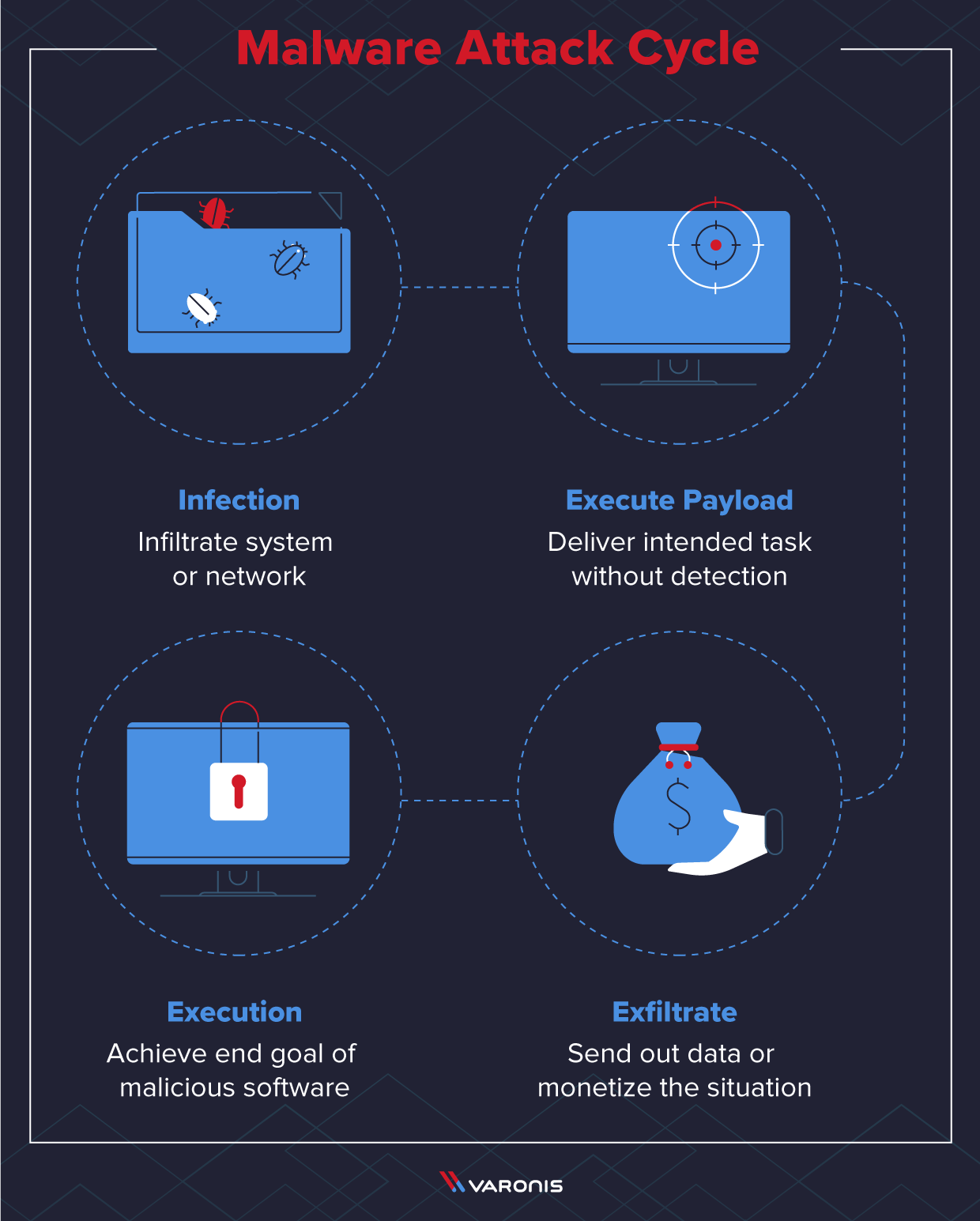
Malware operates in a cycle, hackers just change individual vectors in the approach to accommodate the specific end goal of the malicious software — which is usually monetary related. The observed cycle goes as follows:
1. Infection
One way or another, malware needs to find a way to infiltrate a system or network. There are several different methods to accomplish this, including Phishing, USB devices, and API connections, to name the most popular.
2. Execute Payload
The bread and butter of any malware is the ability to deliver its intended task without detection or prevention successfully.
3. Exfiltrate
Lastly, malicious software needs to be able to finish its task by either sending out the data or giving the malicious actor a way to monetize the situation (ransomware).
The techniques and tactics with each type of malware will differ, but the ultimate goal and cycle remain constant.
Types of Malware
Now that we understand the overall objective of malware, let’s review some of the specific types of malware to get a better understanding of the controls needed to detect and prevent it in our environments. Each of the following types of malicious software will require individual actions to fully identify and remediate successfully within an acceptable amount of time.
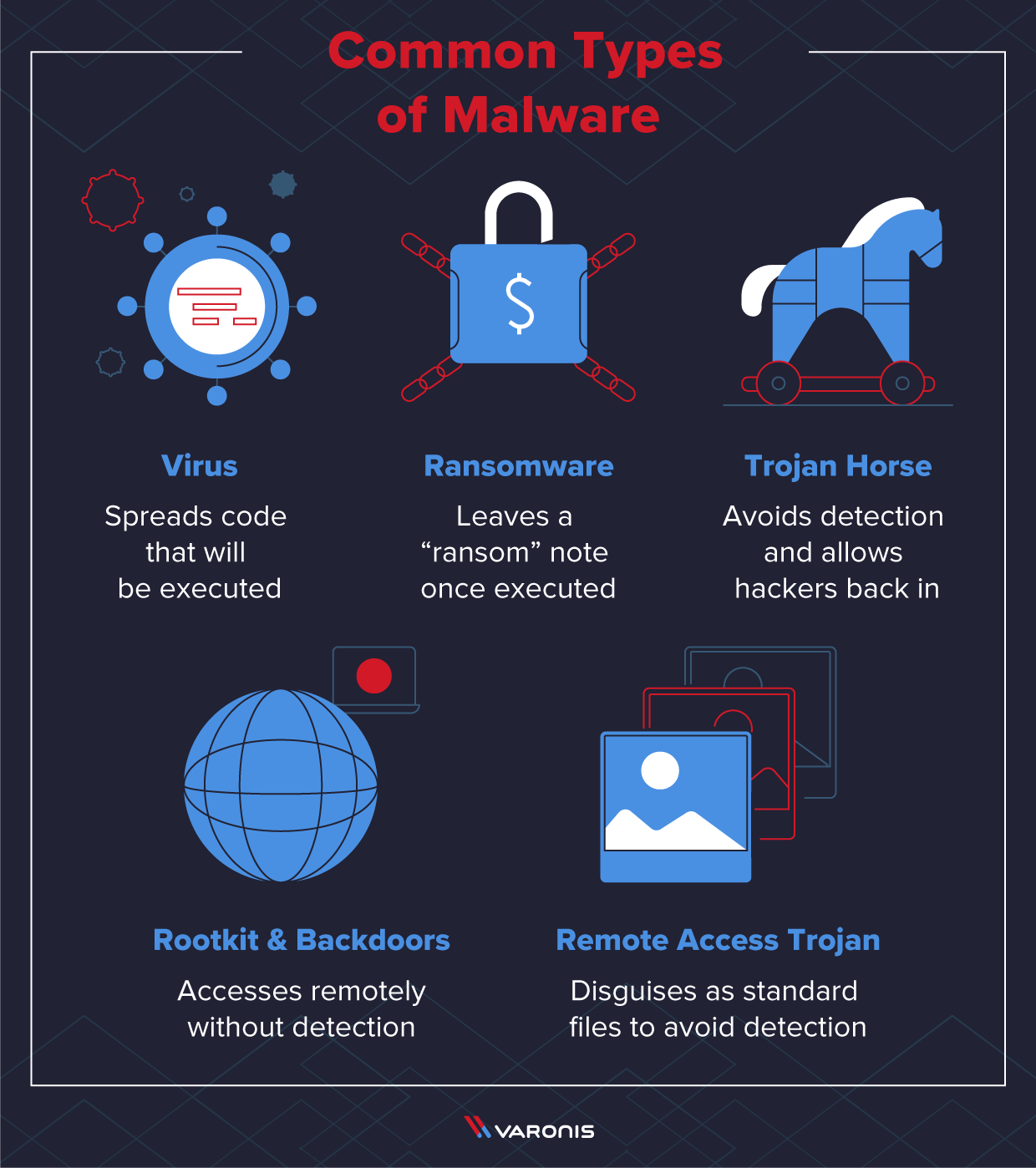
Virus
Over the years, viruses’ purpose has drastically evolved. In the past, Viruses were mostly created only to cause unwanted havoc. Nowadays, criminals have crafted custom viruses to do much deliberate and damaging attacks.
By definition, a virus is a piece of code that will spread to other programs on a computer once it’s executed. The main reason for spreading the virus is to avoid permanent removal. If you remove the original file, it still may live elsewhere on the computer, thus continuing to carry out its sole intention.
Ransomware
Ransomware is one of the more well-known types of malware as news of mass infections has reached the mainstream media. This type of malware encrypts files on a computer or storage system, then leaves behind a note with instructions on how to unencrypt the data (for a price).
The public is urged never to pay the ransom if you are ever affected, as there is no guarantee that the criminals will ever help you get your data unencrypted. It is encouraged that you reach out to your local authority and utilize professional services to help unencrypt your data. Ransomware is one of the top malware types affecting corporations as it is typically very disruptive to a corporate network.
Tip: No More Ransom is a great resource to help determine if there is a publically available decryption key for your encrypted files.
Trojan Horse
Ever heard the story of Troy and the Trojan Horse statue? This aptly named malware aims to successfully invade a system, avoid detection and leave a backdoor in place to give the attacker a way back into the system at a later date. Trojan Horses give cybercriminals a chance to gather intel on the internal system or network and craft deeper attacks specifically tailored to the compromised network.
Rootkits and Backdoors
As mentioned earlier in the article, rootkits and backdoors essentially empower hackers to remotely access and control a system without being detected. Rootkits allow attackers to gain full access “root” to a system where they can then launch new commands, start exfiltrating data or modify logs and programs to avoid detection
Backdoors are the general term for any routes that hackers or insiders leave that allow access remotely or outside of authenticated access to an internal system.
Once attackers can establish a solid backdoor and gain a presence on a network, it can be tough to both remove their access and to forensically determine what data they accessed. Without proper monitoring in place ahead of time it may not be possible.
Remote Access Trojans (RATs)
RATs or Remote Administration Tools are a form of backdoor technique hackers use to gain and keep remote access on a system, a process that is still prevalent today. For a RAT to operate as intended, it needs to have a server-side agent or file that keeps persistence on the network, thus allowing the outside party to maintain control and access. These files are often disguised to look like standard files to avoid detection.
How to Defeat + Prevent Malware with Varonis
Now that we have a high-level understanding of the malicious software being deployed on a day-to-day basis, let’s dive into some of the ways Varonis can provide malware protection and help your organization detect, defend and mitigate against these promptly.
Virus Defense: Malware Prevention with Varonis
Varonis is not your typical, run of the mill malware protection service, Varonis establishes a baseline in your network and helps to categorize events into two main categories; human activity versus machine activity. Varonis and its DatAlert solution help to bring effective detection and prevention alerts to your fingertips with minimal false positives.
By monitoring and creating a baseline of what a typical user in your environment does on a consistent basis, Varonis is then able to make a quick determination if the suspicious activity is common or not. Varonis utilizes standard threat models to help establish this baseline. Each threat model is considered a violation or simply put, an alert that a more significant attack might be underway.
Let’s review some of these threat models in detail and dig into how Varonis can help enforce/ prevent some of these within your enterprise.
Threat Model #1: Encryption of multiple files
How it works: Varonis is looking for two specific vectors in this threat model; multiple file modify events by a user and when those modifications include file extensions that have been deemed malicious. When this criterion is met, the event is triggered.
What it means: This activity is consistent with most modern-day Ransomware attacks, where a user account that doesn’t typically encrypt data (or a lot of data) now is encrypting tons of data in a format that is known around the world as typical of foul actors. Varonis can instantly lock down this machine and user account to prevent any further damage until your tech team has a chance to investigate.
Where it works: Currently, this threat model is supported on the following systems; Windows, Unix, Unix SMB, SharePoint, NetApp, EMC, Hitachi NAS, HP NAS, SharePoint Online, OneDrive, Dell FluidFS, Nasuni.
Threat Model #2: Abnormal Behavior: Unusual number of files deleted
How it works: Varonis DatAlert looks for multiple files that were deleted within a given period as the main criteria for this alert.
What it means: This activity could indicate that several different scenarios could be playing out. A disgruntled employee that just found out they have been fired could be deleting files to cause havoc or a malicious insider trying to cover up their tracks as they plan to steal company secrets. Ultimately, Varonis will prevent this activity from happening further by isolating the user’s profile until it can serve the sole purpose of the file deletions that can be verified.
Where it works: Currently, DatAlert supports the following systems; Windows, Unix, Unix SMB, SharePoint, NetApp, EMC, Hitachi NAS, HP NAS, SharePoint Online, OneDrive, Dell FluidFS, Nasuni.
Threat Model #3: Abnormal Behavior: Unusual number of sensitive files deleted
How it works: This threat model takes the previous a step further by comparing the activity against the Varonis data classification model to help determine if the data being deleted is sensitive data.
What it means: Compared to the previous example, the activity could be the same. A user trying to delete data for malicious reasons or it could be someone simply cleaning up a file share with data that is no longer needed. The action on this alert would be the same, but the violation trigger would be rated as a more significant concern.
Where it works: Windows, Unix, Unix SMB, SharePoint, NetApp, EMC, Hitachi NAS, HP NAS, SharePoint Online, OneDrive, Dell FluidFS, Nasuni
Anti-Malware Solutions with Varonis
Malware defense threat models are where Varonis thrives and where most users see the most consistent malware detection and prevention action occurring. Most activities picked up by these threat vectors contain fewer false positives as system file level activity is not a common action for most users.
The average user within any size company typically should not have any type of backdoor or rootkit level activity occurring on their machine; thus, the rulesets for these threat models are much more aggressive. Let’s review some of the models at a high level to determine how Varonis can help take your security stance to the next level.
Threat Model #4: Suspicious access activity: non-admin access to startup files and scripts
How it works: DatAlert strictly monitors the startup folders on a given machine and alerts on any activity that is performed by a non-admin user. In a typical enterprise environment, standard users should not have full admin access to manage their machine. If they do, Varonis will work with you to help broaden the scope of this alert to cover “any account” activity within the specified folders.
What it means: Varonis is looking for startup level files that may have been tampered with by a malicious actor. A piece of malicious software that is downloaded on a machine can effectively bury itself inside the startup process of the device, thus making it very difficult to get rid of. By doing this, it guarantees the hacker has a persistent way to keep access to the machine.
Varonis counteracts this process by capturing the activity early enough to isolate the trojan and remove it before it can spread and nest itself. By letting the trojan nest, your only option would be to reimage the machine.
Where it works: Currently, Varonis only supports the following systems for threat model 4; Windows, Unix, Unix SMB, HP NAS.
Threat Model #5: Exploitation software accessed
How it works: Varonis keeps a running repository of what tools hackers use to infiltrate systems. Threat model #5 is merely looking for the use of these tools on any system being monitored.
What it means: Unless you are on the security team, you shouldn’t be using some of the open-source hacking tools available on the internet, within a corporate setting. By quickly identifying when and where these tools are being used, the security team can make an informed decision on if this activity is warranted or not.
Where it works: Threat model #5 is supported on; Windows, Unix, Unix SMB, SharePoint, NetApp, EMC, Hitachi NAS, HP NAS, SharePoint Online, OneDrive, Dell FluidFS
Malware Protection From Rootkits and Backdoors
Once a hacker has gained persistence on a device or network, it can be challenging to differentiate between regular activity and abnormal. Luckily, Varonis supports several threat models that are explicitly looking for activity, indicating the presence of a backdoor.
These threat models focus on activity trends and behavior more so than just individual events occurring.
Out of all the threat models supported, those that fall under rootkits and backdoors will need the most attention to fine-tune truly. Once in place, Varonis can help track and identify service accounts that are showing signs of lateral movements within your network as well as other accounts that may have been compromised.
Threat Model #6: Abnormal service behavior: access to atypical files
How it works: Service accounts are the easiest to profile as they usually perform the same set of actions repeatedly, with no user interaction. Varonis will monitor all service accounts for any activities that fall outside of its day to day norm.
What it means: If Varonis detects threat model #6 anywhere in your environment, it is essential to investigate what the actual deviation is about quickly. Hackers will use service accounts as their starting point for triaging an internal network to pursue additional elevated access and sensitive data. It is crucial to investigate these occurrences as soon as possible to isolate a potential threat that may be lingering.
Where it works: Threat model #6 is supported on; Windows, Unix, Unix SMB, SharePoint, NetApp, EMC, Hitachi NAS, HP NAS, SharePoint Online, OneDrive, Dell FluidFS
Threat Model #7: Abnormal admin behavior: an accumulative increase in lockouts for individual admin accounts
How it works: Varonis monitors for an excessive number of lock-out events generated on an account with administrative primitives within a specified period.
What it means: Threat model #7 is looking for admin accounts that a hacker is attempting to login to gain additional, elevated access to the network. An attacker will try to brute force an account they believe has admin privileges to effectively “guess” the password.
In most corporate environments, strict password lockouts are in place to prevent this activity. Varonis can alert on whenever this lockout activity is occurring at an excessive rate, so the SOC team has a chance to isolate the threat.
Where it works: Threat model #7 is currently only supported in Directory Services
Threat Model #8: Membership changes: admin group
How it works: Another example of privilege escalation monitoring is explored within threat model #8. Varonis will detect any account privileges changes that are made outside of the “normal” change control process.
What it means: If a hacker tries to escalate the privileges of one service account with the admin privileges of a standard user account, this will trigger an alert as this activity doesn’t usually happen when granting rights in directory services.
The hacker is attempting to gain access to a specific resource by elevating an account they have access to. Varonis can quickly identify this threat and mark it as pending SOC review to solidify validity.
Where it works: Currently only supported in Directory Services.
Malware Defense Against RATs with Varonis
Monitoring and detection of RAT technology is not a challenge for Varonis. By combining threat intelligence with vectors like geo-location and DNS data, Varonis can quickly pinpoint anomalies on your network perimeter that may be attempting to exfiltrate data.
As an organization, it is essential to understand how your data is accessed, but also how it comes in and how of your control. Let’s explore some threat models that can help narrow in on what’s constituted as data exfiltration.
Threat Model #9: Abnormal behavior: activity from new geo-location to the organization
How it works: Varonis is merely looking for any activity originating from a Geo-location that matches that of a list of threat actors. This threat model can also be tuned to focus solely on geo-location that you do not do business in.
What it means: If your company only does business in the United States, but you see transactions and events generating from a country outside of the US, this is a cause for alarm, and Varonis can immediately help to self-isolate the threat until an investigation can occur.
Where it works: Currently, This model is only supported on your VPN.
Threat Model #10: Data Exfiltration via DNS Tunneling
How it works: Varonis is monitoring your inbound/outbound DNS traffic for several different factors, including; traffic to known malicious sites and non-DNS related commands being sent over DNS.
What it means: If threat model #9 is detected, it is likely that you have a RAT located somewhere on your network, and a threat actor is attempting to communicate with it over the internet. Varonis can take swift action alert on and isolate the threat if desired.
Where it works: This is available over your DNS traffic monitoring.
Remediation + Tips for IT Pros
When it comes to remediation practices there are a couple of overarching themes that should always play a role. No matter the situation you should always hold communication and vigilance as top priorities as well as remembering and using your predetermined protocols.
Communication: It is vital to the success of corporations of any size to have clear communication. Even outside of a crisis, it is essential for implementing security controls across the board. Without a clear channel of communication, you may run into complications that affect other departments or areas of your business (for example, setting up restrictive controls).
Stay Vigilant: No matter the solution or process you have in place for detecting and responding to vulnerabilities, it is crucial you do so promptly. Tackling alerts early on helps prevent further damage.
Game Plan: Last, but not least, make sure there is a response plan in place for when an incident does occur. This response plan of action should be practiced a couple of times a year. Having all parties involved in these sessions will ease tension and mistakes when the real thing happens.
Whether you are a security professional or someone that is in charge of the security for your company. The threats mentioned above are real and occur to all size companies on a day-to-day basis. You must understand your data and your options for securing it.
Check out free trials and tutorials of how tools like DatAlert and DatAdvantage can give you the peace of mind that your security is being taken care of.
What you should do now
Below are three ways we can help you begin your journey to reducing data risk at your company:
- Schedule a demo session with us, where we can show you around, answer your questions, and help you see if Varonis is right for you.
- Download our free report and learn the risks associated with SaaS data exposure.
- Share this blog post with someone you know who'd enjoy reading it. Share it with them via email, LinkedIn, Reddit, or Facebook.