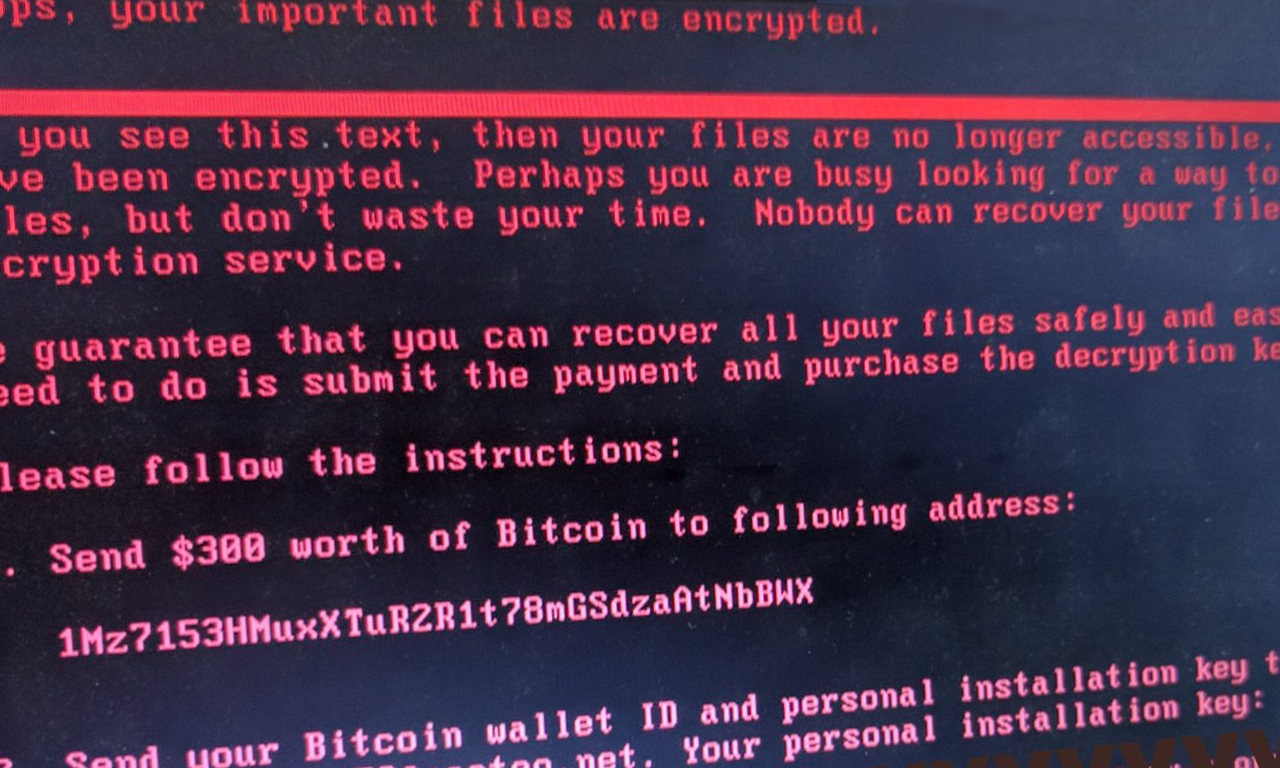
Explosive ransomware infection rates of WannaCrypt/WannaCry have IT groups trying to mass diagnose, update and protect their machines. Thing is, that’s just not practical to do manually – for pretty much any but the smallest of organizations.
While there are a number of different PowerShell scripts that have been open sourced in the last three days to automate this (we link to the best one below), it’s quite likely that they won’t necessarily cover exactly what you need them to do on your network.
Get the Free Pentesting Active
Directory Environments e-book
Further, it’s guaranteed that there will be multiple variants, mutations and other forms of Wannacrypt that will continue to appear in the coming months. Being able to build your own script or to tweak one to your needs may be essential in keeping your network secure.
To help, we’ve collected all of the different Powershell utilities needed to help with WannaCrypt / WannaCry:
- Use PowerShell to check if a particular Hotfix is installed
- How to import TCP/IP functionality into your script to check which ports are open or closed (such as SMBv1’s port 445)
- How to check if a domain resolves properly with PowerShell (like the Wannacrypt killswitch domain)
- How to disable SMBv1 functionality with Powershell
First: use the following script from Github User Kiernanwalsh to check for missing patches. The script is a collective effort as multiple members of the community are submitting missing KBs, and offering suggestions.
https://github.com/kieranwalsh/PowerShell/blob/master/Get-WannaCryPatchState/Get-WannaCryPatchState.ps1
How to use PowerShell to check if a hotfix is installed
Get-Hotfix tests the local machine (by default) or a remote workstation or server for the presence of a specified hotfix (referenced by it’s KB designation).
For reference, the KB’s per operating system to patch MS17-010 are:
Windows Server 2008
KB4012212
Windows Server 2012
KB4012217, KB4015551, KB4019216
Windows Server 2012 R2
KB4012216, KB4015550, KB4019215
Windows Server 2016
KB4013429, KB4019472, KB4015217, KB4015438, KB4016635
Example
The examples below check for KB4012212 which is the Windows Server 2008 patch for MS17-010.
Local
get-hotfix -id KB4012212
Remote
get-hotfix -id KB4012212 -computername <remote-computer-name>
PowerShell Port Checking
Use the Test-NetConnection cmdlet to test if a port is open on a remote computer. In the example below, we’re testing if 445 (command and control port for Wannacrypt) is open on the local interface.
Test-NetConnection -ComputerName 127.0.0.1 -Port 445
Several important things to note:
- The port being closed doesn’t prevent the infection of that machine, just prevents infecting other hosts.
- Test-NetConnection doesn’t default to the local machine – but to a designated test server run by Microsoft. You MUST specify the `-ComputerName` parameter.
Testing if a domain resolves with PowerShell
The first version of Wannacrypt/WannaCry contained a killswitch which shut it down if the script was able to successfully connect to a previously unregistered domain.
http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com
A security researcher registered the domain and was able to stop a large number of the infected machines from spreading further.
Even after the domain was registered, however, many networks were unable to connect due to outbound filtering, DNS caching issues, or other network restrictions.
To test if a machine is properly resolving a domain use the Resolve-DnsName cmdlet:
Resolve-DnsName www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com
How to disable SMBv1 with PowerShell
As of right now, having SMBv1 enabled is the key exploitable aspect of pre Windows 10 machines. While you should still endeavor to install the appropriate patch to handle MS-17-010, disabling SMBv1 immediately can help prevent infection.
On Windows 8 and Windows Server 2012
Set-SmbServerConfiguration -EnableSMB1Protocol $false
Will take effect immediately, no restart required.
On Windows 7, Windows Server 2008 R2, Windows Vista, and Windows Server 2008
Set-ItemProperty -Path "HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters" SMB1 -Type DWORD -Value 0 -Force
This will require a restart to take effect.
Conclusion
WannaCrypt is a mess for everyone involved. But! The cleanup is a great place to polish your PowerShell skills and make process and infrastructure investments to prevent issues in the future.
What you should do now
Below are three ways we can help you begin your journey to reducing data risk at your company:
- Schedule a demo session with us, where we can show you around, answer your questions, and help you see if Varonis is right for you.
- Download our free report and learn the risks associated with SaaS data exposure.
- Share this blog post with someone you know who'd enjoy reading it. Share it with them via email, LinkedIn, Reddit, or Facebook.