In a world where news spreads fast and online reputation is everything, cyber-attacks and data breaches are a massive threat to organizations across the world. Data breaches are among the top three threats to global stability and the average cost of a data breach is $3.86 million. Aside from the financial costs, reputations take a big hit and some never quite recover. When the overall costs of insufficient security are laid out, it’s clear that a solid cybersecurity strategy is crucial to every organization and a healthy cybersecurity budget is worth the investment.
So if you’re ready to level up your security, one of the most important places to start is with your employees and their knowledge and use of cybersecurity best practices. The cybersecurity tips below cover awareness, basic safety, online safety, social media, data security, tips for remote workers, small businesses and considerations for CEOs and CISOs to keep in mind.
Get the Free Pentesting Active
Directory Environments E-Book
Awareness Is Key: How to Make Employees Care
The first step to better security across your organization is to make employees more aware. They’re your greatest asset when it comes to security, and your greatest liability. Making employees think of cybersecurity as a top priority is easier said than done when they have todo lists and deadlines of their own. Use the tips below to give it your best shot — these will help train, inform and make your employees care more about the role they play in the cybersecurity of your organization.
- Show them what’s in it for them. So much of what employees learn during at-work security training can be applied to their personal account safety. Show them the value of the information as it pertains to their safety and security, not just the company’s interests.
- Make it clear that no one is safe from an attack. It’s not a question of if but when it happens, then how quickly and effectively team members can react to block the attack or minimize the damage.
- Start awareness training during onboarding. It’s never too early to learn good habits. It makes a lot of sense to integrate cybersecurity into the onboarding process as new employees are likely gaining access to accounts, making their passwords and learning about company processes.
- Create an official cybersecurity training plan. To go with the tip above, there should be an organized training plan in place for employees that is updated as necessary and accessible.
- Talk about data ethics. “When employees think about data ethically, like thinking about the human, the person, or the family the data represents, data breaches are less likely and their impact could be reduced.”
– Neal O’Farrell, cybersecurity expert and founder of the Identity Theft Council
- Educate on Data Privacy Policies. Teach employees that just because some data is available that the usage of that data may be restricted. As an example, most companies maintain lists of contacts who have opted out of receiving any further sales emails. Individuals emailing them violate this policy.
- Bring in professional cybersecurity awareness and training experts. These trained professionals can engage employees and lay out the basics and specifics that they should know for their job.
- Conduct cybersecurity “emergency” simulations set up by your internal security team or an outside source. These simulations should be tailored to specific job roles and focus on attacks that employees could receive so they can learn specific takeaways and areas to improve.
- Send regular updates on the protocol, threats, new scams and viruses, software updates and other important cybersecurity information.
- Communicate clearly and concisely. “Try to stay away from long emails and memos that a lot of employees will skim the first couple of sentences before deleting. Instead, try creating some videos, or maybe hang up some infographics in main areas of the office, like the break room or near the water fountain… Even if your employees aren’t that interested in security, repeatedly reading phrases and actions in visual form will help them remember said messages when something out of the ordinary occurs.”
– Marty Puranik, co-founder, CEO and President of Atlantic.Net
- Hold regular security training. “As new threats and patterns of threats emerge, regular security training must be implemented on an enterprise wide level, to make sure the kinds of security holes that allow malicious activity to penetrate the enterprise are not exposed.”
– Bryan Osima, software engineer and CEO of Uvietech Software Solutions Inc.
- Recognize and reward employees who report malicious emails or other attacks. With so many other things on their minds, this will help keep security at the forefront.
- Create a cybersecurity-friendly culture by appointing advocates and keeping employees motivated overall to maintain the integrity of your cybersecurity best practices.
- Set the tone at the top. “Business owners are responsible for setting the company culture. Owners who take cybersecurity seriously will influence their employees to do the same. Make cybersecurity part of the workplace conversation.”
– Peter Purcell, cybersecurity expert and co-founder of EVAN
Cybersecurity Tips for the Workplace
We’ve gathered the most effective and important cybersecurity safety tips to keep in mind for prevention and risk mitigation. Included are some baseline security tips, as well as online safety tips including best practices for browsing, email security and other online activity. We also include guidance on social media safety that focuses specifically on social media practices and the best ways to keep those accounts safe, as well as special considerations for remote workers, CEOs, CISOs and small businesses.
Basic Cybersecurity Tips
- Virtually and physically lock up devices, assets and data storage. Make sure you lock your device any time you leave it unattended and also make sure devices auto-lock when idle and services are set to aggressively time out when not used. This also applies to rooms or storage locations that contain sensitive information or devices.
- Use a Password Manager. Password managers generate unique complex passwords for each site and service. Don’t use the same password for multiple sites, and always use a unique mix of upper and lower case letters, numbers and other characters. “Sure, there is usually a minimum recommendation of eight characters – but if you follow that rule, you are making it easier for hackers to crack that password. As a rule, always use double the minimum amount of characters or even more.”
– Joe Flanagan, Security App Developer at GetSongbpm
- Use multi-factor authentication for additional layers of security and to make sure important accounts aren’t easily hacked if the passwords are cracked. Preferentially use non-SMS-based MFA options.
- Encrypt your data, it adds an extra layer of security should your data ever be compromised.
- Back up data often. If data storage is ever compromised, you’ll have the best chance of hanging on to that data if you have a secure backup.
- Monitor your network for suspicious activity, so that you can catch on to an attack early enough to reduce the damage.
- Be wary of external devices, such as hard drives, flash drives and smartphones, as they can infect your computer when plugged in.
- Never share sensitive information with an unauthorized party. This may sound obvious but all too often employees feel some sort of social pressure when someone else asks them for information (this applies to people within your organization too). If there’s any doubt, say no and consult a manager for permission.
- Don’t underestimate hackers’ interest in your company because it’s smaller or just starting out — breaches and attacks affect organizations of all sizes, including start-ups and small businesses. Many offensive security tools indiscriminately scan the Internet for vulnerabilities in services, remote access, and web applications.
Cybersecurity Tips for Online Safety
- Use VPNs (Virtual Private Networks). They extend your network protection past your private network when you’re on other sites. If someone is able to intercept your data online, all they will be left with is encrypted data.
- Always verify financial transactions with a manager or CFO before taking any action or sending funds.
- Verify informational transactions with a manager or CISO. Never send sensitive data or passwords.
- Use caution when shopping or banking online for the company, only use company-sanctioned secure devices that belong to you and secure WiFi/networks when handling these tasks.
- Be careful about what you share on social media. Whether you are on a personal or work account, criminals can gain insights from sensitive data you share that can help them target you.
- Phishing scam awareness. Make sure employees are educated about the signs of a phishing scam:
- Slow down and evaluate emails carefully before clicking or taking action.
- Enable mail server options to explicitly label emails that originate from outside the company.
- Never click links from an unknown sender before carefully vetting the URL. They may pose as someone from your company or a reputable company, use a URL similar to a well-known site, use logos and disguised email accounts — pay close attention to detail.
- Keep an eye out for strange requests, spelling and grammar mistakes, flashy click-bait content and other things that may seem “off.”
Cybersecurity Tips for Your Remote Workforce
- Specialized remote worker training is very important as the popularity of remote work rises. This also includes on-site employees who occasionally work from home or while traveling.
- If you have a BYOD (bring your own device) policy, use MDM (mobile device management). This will give you the power to wipe a device clean remotely should a device be stolen or lost.
- Only work on trusted secure networks and devices. Free WiFi or public computers may be alluring, but these are easy tickets for a hacker to gain access to your accounts and information.
- Provide cellular WiFi hotspots or tethering plans. Provide remote workers with portable WiFi hotspots that can be used instead of allowing connections through Public WiFi networks. These hotspots can help regulate access and should be password and login protected as well.
SME Owners, CEO and CISO Considerations
- Properly prioritize security risks. “Many organizations are doing a poor job of prioritizing information security risks appropriately. Part of this is a product of how the information is presented and the context within which it is presented. Information security risk assessments and maturity assessments are long, overly complicated, and difficult to distill down to a prioritized roadmap… The solution revolves around communication. Basing the message in terms of risk to the organization, and having that be the core of your reporting is essential.”
– Christopher Gerg, CISO and Vice President of Cyber Risk Management at Tetra Defense
- Strive for open communication between board members, C-Suite and the IT team. “When I am engaged to investigate and report, it ordinarily is an issue that could have been resolved without outside counsel, but a lack of clear communications between IT and the Board stymied that understanding. It’s imperative in most companies to have a Board member knowledgeable in the area that can understand and communicate issues related to IT security and have a voice in an area that most board members don’t understand.”
– Braden Perry, cybersecurity attorney at Kennyhertz Perry, LLC
- Offer extra training. Give employees, especially those in the line of (cyberattack) fire, the option to continue their cybersecurity training and learn new preventative and defensive skills.
- Conduct periodic assessments of your software performance as well as employee knowledge. This will help you determine where your weaknesses are and if the company needs a refresher course on security best practices.
- Set expiring passwords and accounts to limit stale accounts or ghost users from compromising your security. The 2019 data risk report showed that 61% of companies had over 500 user accounts with passwords that never expire.
- When employees leave the company, make sure to revoke their access, credentials and privileges. If left unchecked, employees could take information to a competitor or provide access to a malicious party.
- Get rid of stale data. It poses an undue threat and risk of sensitive data exposure should a breach occur. Purge your database of data that’s no longer needed. Highlights from the data risk report also showed that 53% of companies’ data is stale.
- Update software in a timely manner to make sure your defenses and networks are the best that they can be. Make sure employees update when needed.
- Delegate responsibility. Appoint security experts who report to the CISO to oversee different sectors of the company.
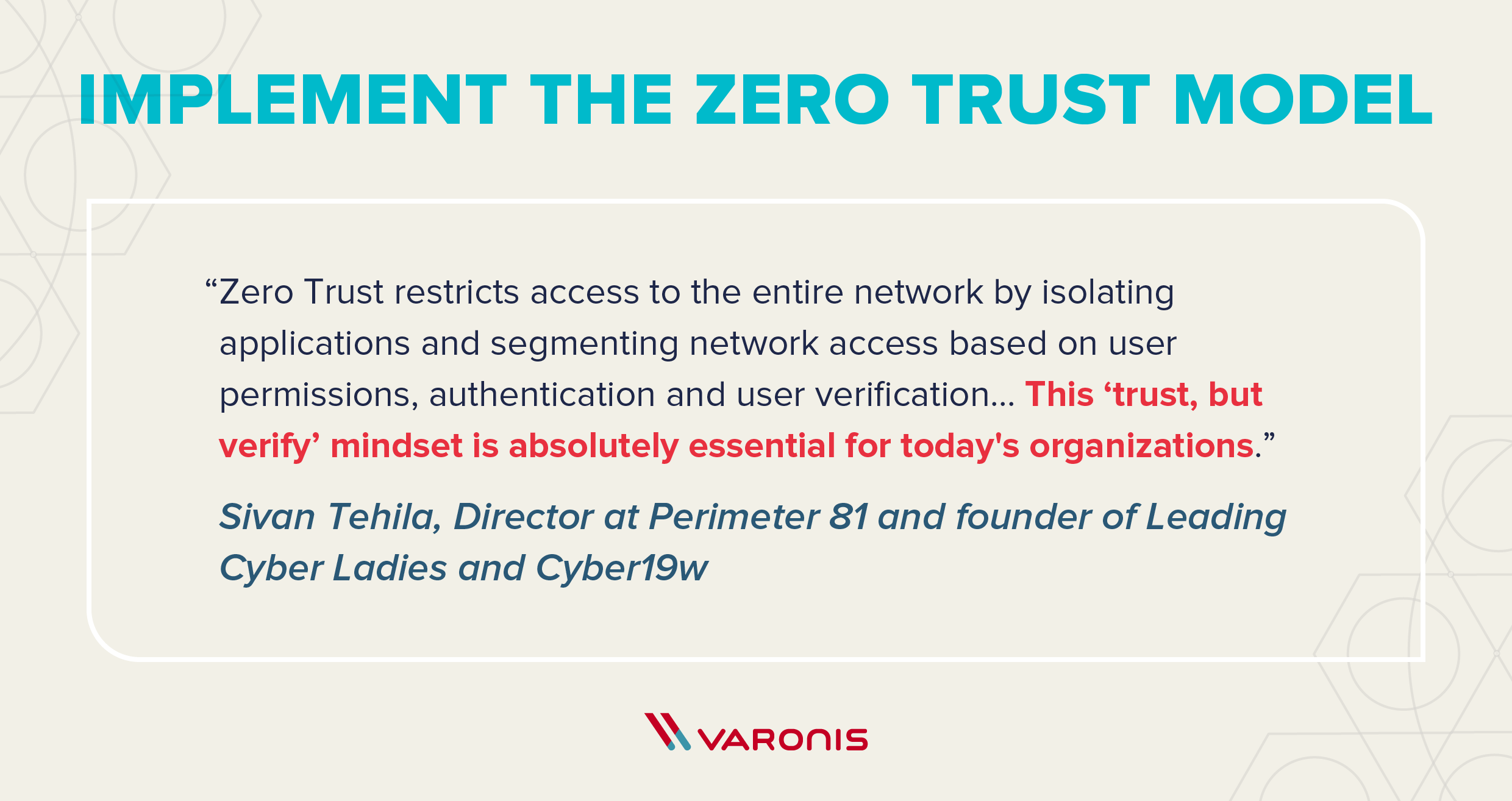
- Implement the zero trust model. “Zero Trust restricts access to the entire network by isolating applications and segmenting network access based on user permissions, authentication and user verification. With Zero Trust policy enforcement and protection are easily implemented for all users, devices, applications and data, regardless of where users are connecting from. This user-centric approach makes the verification of authorized entities mandatory, not optional. This ‘trust, but verify’ mindset is absolutely essential for today’s organizations.”
– Sivan Tehila, Director of Solution Architecture at Perimeter 81 and founder of Leading Cyber Ladies and Cyber19w
- Make sure data is classified correctly, because if it isn’t, then you won’t be able to properly control who is supposed to have access to it — data governance is key especially when dealing with sensitive data like in areas like education, healthcare, finance and government.
- Properly propagate and grant permissions and access to files and folders. Only grant access when it’s absolutely necessary.
- Use RBAC (role-based access control). This streamlines the process of permissions by assigning different departments and sectors different permissions. For example, you can set it up so the head of finances and the team they manage automatically gain access to the files and folders that pertain to their work.
- Collaborate and seek consultation from other experts. “Organizations need to adopt open and share details in public about what we do for cybersecurity. Bad guys spend all day probing good guys and all night collaborating to make tomorrow’s probes better. Good guys need to level the playing field. Better to be embarrassed by our peers than victimized by attackers.”
– Greg Scott, IT expert and founder of Infrasupport
- Stay on the cutting edge of security so you can be prepared for all of the different viruses and new hacking methods that are constantly being deployed. Follow cybersecurity news or consult with experts to stay ahead.
Click the button below to download a playbook with our top 15 tips from this list.
With better employee awareness and training, you’ll significantly reduce your insider threats. When it comes to scenarios out of your control, Edge addresses external threats by setting a personalized baseline of normal activity and monitors for abnormal activity. If an abnormality is detected, you will be sent a link to a detailed investigation report. The combination of proper training and world-class security technology is a cybersecurity match made in heaven — try a free risk assessment or free demo to see if it’s a match made for you.
What you should do now
Below are three ways we can help you begin your journey to reducing data risk at your company:
- Schedule a demo session with us, where we can show you around, answer your questions, and help you see if Varonis is right for you.
- Download our free report and learn the risks associated with SaaS data exposure.
- Share this blog post with someone you know who'd enjoy reading it. Share it with them via email, LinkedIn, Reddit, or Facebook.