From a business perspective, distribution lists (DLs) for email communications are a powerful and well-understood concept in IT. And they are popular: Exchange admins have voted with their right-clicks, creating lots of these Active Directory objects in their corporate domains. DLs speed up overall collaboration and leverage the power of groups to answer questions, share and inspire ideas, and announce news. For a number of years, the Linux operating system was developed and maintained by submitting patches via a mailing list.
With the wonderful simplicity and utility of distribution lists, what could possibly go wrong?
Is your Office 365 and Teams data as secure as it could be? Find out with our Free Video Course.
As it turns out, managing DLs can be a headache. Like everything else in IT, they have a life cycle: they’re born, they’re used, and then they become less relevant. As employees migrate to new areas and gain other responsibilities, the distribution list should be updated as well. But they are not. Often the managers who rely on these DLs are too busy to tell IT to weed out an alumni, and/or add a new freshmen. Bottom line: there are likely many distribution lists within an organization that are either unnecessary or are no longer serving their original purpose.
Investigating Current Options
Many organizations are very likely managing distribution lists in Exchange or mail-enabling security groups, so we’ll address the pros and cons of these methods below.
Distribution Lists in Exchange
Since the advent of Exchange, distribution lists have existed and have been used to send information to a group of users via a single email address. As soon as the email reaches the server it distributes the message to all members. You can even allow every user to see (or not see) which users are included in the group itself. However, the main disadvantage of managing distribution lists in Exchange is that IT is tasked to manually add and remove users.
Mail –Enabled Security Groups
If you have a group of users who need access to similar resources, and often need to send e-mail to this same group of users, you might want to consider mail-enabling universal security groups.
Mail-enabled security groups are effective as long as all members of the security group want to be on the distribution list. Realistically, you’ll encounter situations where additional users will require access to some of the restricted folders but do not want to be on the distribution list. This means they’ll have to be manually added and removed on each folder instead of just being made members of the security group. The opposite may also be true, where users that shouldn’t have access to the resources granted by the mail-enabled security group want to be on the distribution list, which will mean you’ll need a new distribution list, anyway.
Overall, if you have a scenario where there is a perfect 1:1 relationship between the security group and the DL, mail-enabled security groups can be a good idea. But remember: you can’t opt users out without revoking their access, so it can get messy fast.
Manual Challenges Remain
Exchange distribution lists and mail-enabled security groups are, in general, awesome features, but they still don’t resolve the manual challenges of managing memberships. If we want the ability to reduce IT overhead and streamline processes, there is a better way.
Delegate DL management to business users and automate with DataPrivilege
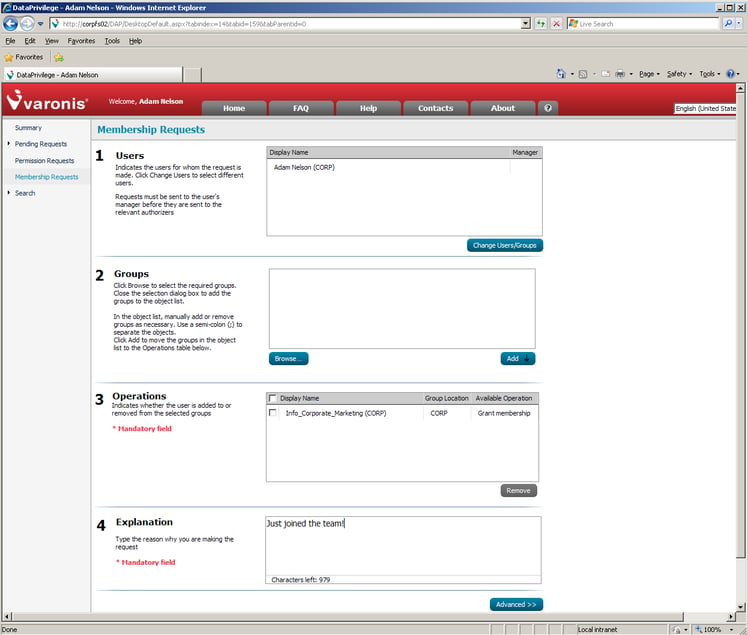
To reduce IT admins’ distribution list burdens, let’s enlist the help of data owners. Varonis DataPrivilege is our web-based interface that’s designed to give managers from the business side the power to authorize and revoke access.
Once a distribution list owner is set, they can independently manage memberships, and automate the membership request process. Data owners can even authorize other individuals to regularly review, authorize or revoke access, because, let’s face it, even data owners need help sometimes.
Give DataPrivilege a spin (it’s free to try) to streamline and automate distribution list management, allowing IT admins to focus their energies on managing technology, not business rules.
What you should do now
Below are three ways we can help you begin your journey to reducing data risk at your company:
- Schedule a demo session with us, where we can show you around, answer your questions, and help you see if Varonis is right for you.
- Download our free report and learn the risks associated with SaaS data exposure.
- Share this blog post with someone you know who'd enjoy reading it. Share it with them via email, LinkedIn, Reddit, or Facebook.




