Ransomware as a service (RaaS) is a major threat to all cybersecurity data and systems. Similar to Software-as-a-Service, RaaS provides easy subscription-based access to ransomware to those with little-to-no programming expertise.
With the popularity of RaaS growing, companies and organizations of all shapes and sizes should be well-versed in reducing the chances they’ll be victimized by a RaaS attack. We’ll cover what RaaS is, how the business model and technology works, and how to prevent attacks.
Get a Free Data Risk Assessment
What is Ransomware as a Service (RaaS)?
RaaS is a subscription-based model that enables users, also known as affiliates, to use ransomware tools to execute attacks. As opposed to normal ransomware, RaaS is a provider of out-of-the-box ransomware tools to subscribers who pay to be an affiliate of the program. Stemming from Software-as-a-Service (SaaS), RaaS affiliates are paying for the ongoing use of malicious software.
Some affiliates pay less than $100 per month while others pay upwards of $1,000. Regardless of the subscription cost, affiliates earn a percentage of each successful ransom payment following an attack. RaaS enables malicious attacks with lucrative rewards to be collected effortlessly, even by users with no prior knowledge or experience in the field. Cerber is one example of a popular RaaS on the market.
How does Ransomware-as-a-Service Work?
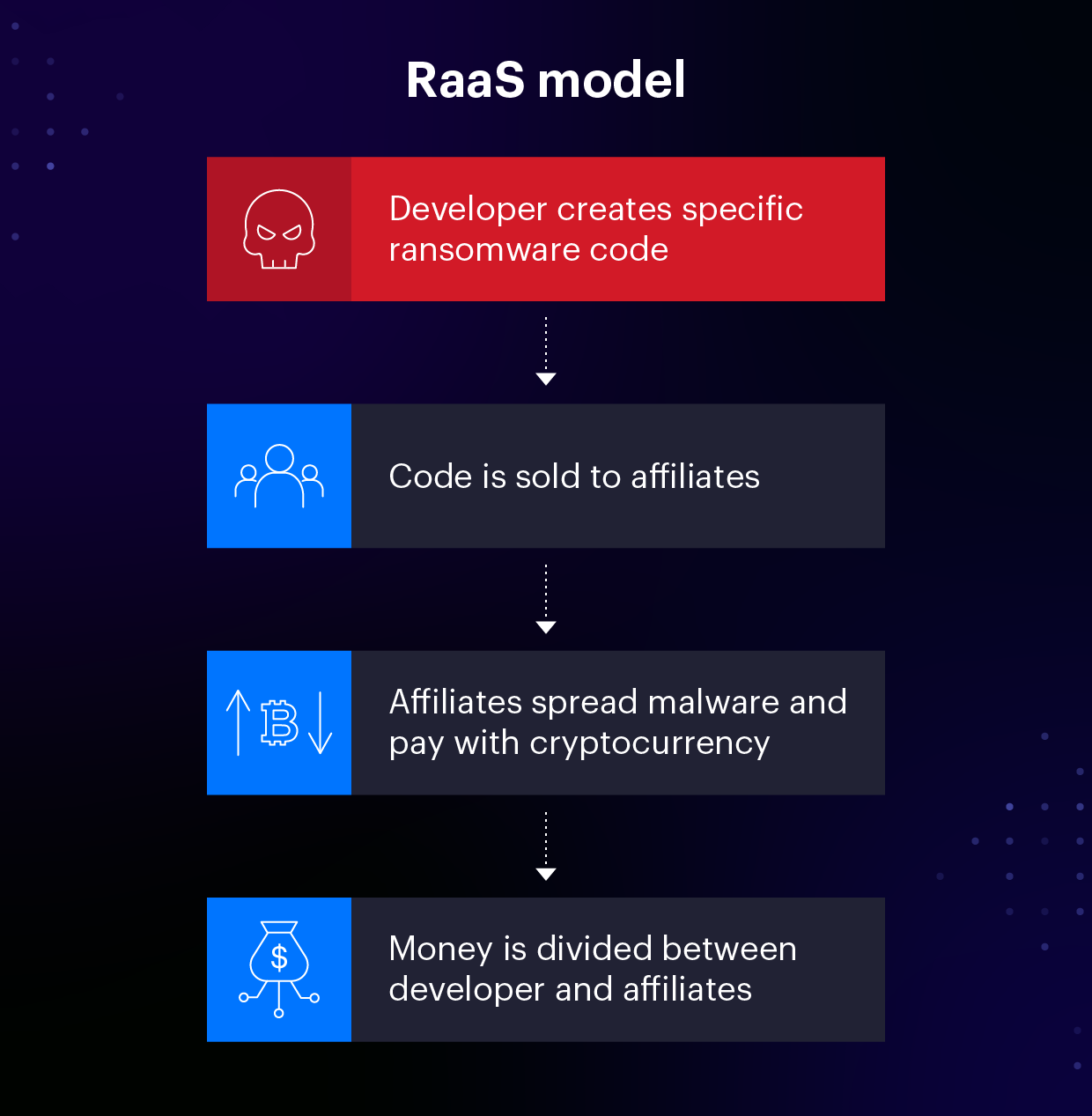
Two parties work together to execute a successful RaaS attack: Developers and Affiliates. Developers are responsible for creating a specific code within the ransomware which is then sold to an affiliate. Developers provide the ransomware code along with instructions on how to launch the attack. RaaS is user-friendly and requires minimal technical expertise. Any individual with access to the dark web can log into the portal, become an affiliate, and initiate attacks at the click of a button.
To get started, affiliates select the type of malware they wish to spread and pay with some form of cryptocurrency, typically Bitcoin. Once the attack is successful and ransom money is received, the profits are split between the developer and the affiliate. How the money is divided is dependent upon the type of revenue model.
The Four RaaS Revenue Models
Most RaaS arrangements fall under one of the four following revenue models:
- Monthly Subscription. Users pay a flat fee on a monthly basis and earn a small percentage of each successful ransom.
- Affiliate Programs A small percent of profits go to the RaaS operator with the goal of running a more efficient service and increasing profits.
- One-time License Fee. As the name of the model indicates, users pay a one-time fee with no profit sharing. Affiliates then have access in perpetuity.
- Pure Profit Sharing. Profits are divided among users and operators with pre-determined percentages upon the license purchase.
Once you familiarize yourself with how RaaS works and the various profit models, you should then begin formulating a plan of defense.
How to Prevent Raas Attacks
Advances in technology have made it easier for code developers and affiliates to infiltrate systems and extract lucrative ransoms from organizations. Ransomware attacks have increased by 33 percent since 2019 with affiliates making up to 80 percent from each payment. To prevent yourself from becoming one of these statistics, here are four must-know tips to prevent RaaS attacks.
1. Backup Data Consistently
Confidential and private data is typically the main target of a RaaS attack. Hackers compromise your systems or data then threaten to steal or release it if the ransom isn’t met. By backing up data, RaaS attackers won’t have the same leverage as they would if they’re in sole possession. So don’t solely rely on cloud storage, backup your data on external hard drives as a preventative measure against RaaS.
2. Keep Software Updated
Another efficient way to prevent RaaS attacks is to keep your system software up to date. This includes your anti-virus measures. Systems using older versions are an obvious weakness that cyber-criminals are keen to exploit. Software updates also increase network security by patching vulnerabilities and ensuring bug fixes. Also, maintain a rigorous patch program to protect from both known vulnerabilities and potential new RaaS technologies.
3. Ongoing Employee Training
RaaS attackers often trick victims with phishing emails that contain malicious links and attachments. If the message is from an unknown sender or it raises skepticism, personnel should already know to avoid it immediately. Train users on how to identify, quarantine, and report malicious messages to avoid unnecessary damage. Conduct regular and updated training on common RaaS tactics like phishing and social engineering.
4. Proactive Detection & Protection
In addition to keeping your cybersecurity software updated, you’ll want to employ technology that focuses on endpoint protection and threat detection. You’ll want your defenses running on an ongoing, 24/7 basis to protect against RaaS at all times. There are many programs to consider that implement a variety of smart tools to detect and remove ransomware threats. For example, DatAlert notifies companies of potential threats and provides insights into suspicious activity and events across multiple data points
The Future of RaaS
Moving forward, RaaS attacks are only going to increase in frequency and popularity amongst cybercriminals. One recent survey found that over 60 percent of all cyberattacks in the past 18 months were RaaS in nature. The ease of use -- and the fact that no technical experience is required -- is only broadening the appeal of RaaS.
We can also expect an uptick in RaaS attacks focusing on critical infrastructure. This includes healthcare, government, transportation, and energy. As supply chain difficulties persist through 2022, hackers see these key sectors and institutions as more vulnerable than ever, putting things like hospitals and power plants in the crosshairs of RaaS attackers.
One of the more popular RaaS platforms on the market, Netwalker, has been specifically targeting healthcare and educational institutions. And to defend against these types of RaaS efforts, it’s likely that organizations will invest even more heavily in both proactive threat detection and employee training to reduce human error as a point of failure.
RaaS FAQs
What’s the definition of RaaS?
Ransomware-as-a-Service (RaaS) is a malicious, subscription-based business model where ransomware operators lease out malware to affiliates via the dark web. RaaS operators usually receive a percentage of ransom payments gained during RaaS campaigns. It’s extremely similar to the legal Software-as-a-Service (SaaS) business model.
How do governments view the legality of RaaS?
RaaS is viewed as an illegal enterprise by most jurisdictions. Being involved in a ransomware attack in any part of a campaign is entirely illegal. This includes buying ransomware kits on the dark web, breaching a corporate network, stealing, encrypting, and downloading system files, and extorting cryptocurrency from victims.
How fast is RaaS spreading amongst hackers?
Quickly Some malware developers create their own attack playbooks and make them available to affiliates. Therefore, various attack groups end up implementing similar attacks. The more that specialist ransomware programmers outsource their malicious code and infrastructure to third-party affiliates, the more the size and scope of ransomware delivery methods will grow.
Closing Thoughts
The unfortunate reality is that RaaS looks like it’s here to stay for the time being. To safeguard against RaaS attacks, you’ll need a holistic technology and cybersecurity strategy to minimize the chances of a successful RaaS attack. You’ll also want to strongly consider enlisting an experienced ransomware prevention partner like Varonis to keep your defenses up around the clock and avoid paying hefty sums of Bitcoin to get your critical data and systems back.
What you should do now
Below are three ways we can help you begin your journey to reducing data risk at your company:
- Schedule a demo session with us, where we can show you around, answer your questions, and help you see if Varonis is right for you.
- Download our free report and learn the risks associated with SaaS data exposure.
- Share this blog post with someone you know who'd enjoy reading it. Share it with them via email, LinkedIn, Reddit, or Facebook.