More devices than ever. More platforms to choose from. An expanding universe of data choices that can be both exciting and confusing at the same time. Tablets, phablets, laptops, iOS, Android, Windows, UNIX/Linux file servers, and NAS devices. Add SharePoint, Dropbox, Google Drive, and LinkedIn to the mix. These are all awesome platforms for allowing businesses, organizations, and individuals to connect and collaborate on documents and projects through portals.
Let’s not forget our complex love/hate relationship with Exchange and its central role in storing emails, documents, calendars, and tasks for most organizations on this planet. Meanwhile, Google is fast becoming a contender with its app environment.
Get the Free Pentesting Active
Directory Environments e-book
Result?
New files, sites, and emails are coming into existence every second of every day. They build up, become unmanageable, and would benefit from routine management and housekeeping—and perhaps some Feng Shui.
Therefore, administrators need to be able to answer some basic questions about their data, including:
- Who has access to the company’s files, sites or mailbox?
- Who should and shouldn’t have access to them?
and
- To whom do they belong?
What’s stopping us from getting a handle on our data dilemma? We’ve come up with some of the major barriers.
Too Much Data
A typical terabyte contains about 50,000 folders, and about 5%, or 2,500 of those folders have unique permissions that need to be managed.
To begin managing these folders, what are things you’ll need to look at – say in Windows? You’ll want to check out the Access Control Lists, Security Groups, Nested Groups and more.
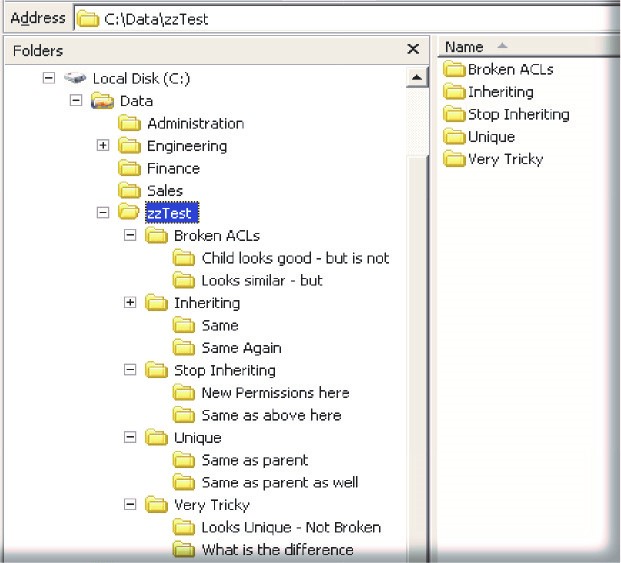
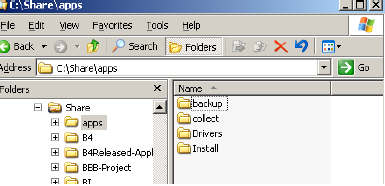
Let’s see what it would look like in a native interface when child folders inherit the permissions of the parent’s and in some insistences they don’t. In the image below, under the folder “zzTest,” there are a few child folders, each with very different and unique permissions. Typical Windows administration tools do not give the administrator insight into the permission levels, inheritance, and uniqueness. This lack of visibility is most often the culprit for allowing users access to data they should not have access to.
Eccentric Permissions
When you begin to manage permissions, security groups, etc, they often have their own idiosyncrasies you’ll need to be aware of. I’d like to go through a few of them with you.
Broken Inheritance
Folders that inherit permissions from their parent are the easiest to manage. When a change is made at the parent level, that change is immediately seen on all child folders that are being inherited.
However, in Windows, when an ACL is “broken,” it means that the NTFS inheritance is not functioning properly. Either the child folder has not properly inherited permissions that it should have, or it is inheriting permissions that are not applied to the parent. Either way it’s a problem and you’ll need a way to find and fix the broken ACLS.
Nested Groups
Security groups often contain nested groups—groups that contain other groups, etc. If a group is a member of itself, there could be an infinite tree path which recursively lists the looping groups. This can slow down your process during directory searches and routine maintenance.
POSIX ACLs
POSIX ACLs provide administrators the ability to assign multiple group permissions to a UNIX/Linux folder. However, many haven’t implemented POSIX ACLS because they don’t have the ability to visualize which permissions exist for each folder.
Impersonation
Exchange impersonation enables a user with a single account to access many accounts. Problems may arise when you’re unable to audit event types: for instance, to identify who did what – message edited, message sent on behalf, message marked as unread, message sent as, message deleted. Any mail that is modified by using impersonation will appear to the mailbox as if it was modified by the user who was impersonated.
Global Groups
Global group permissions often pose a problem because their access is much broader than necessary. It’s a common problem because this is the default permissions setting when a folder is created on a Windows server. Sensitive data – such as credit card numbers, social security numbers, patient and patent information could reside in these folders and accessible by, unfortunately, everyone.
Who’s eating my porridge?
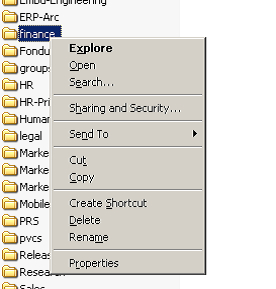
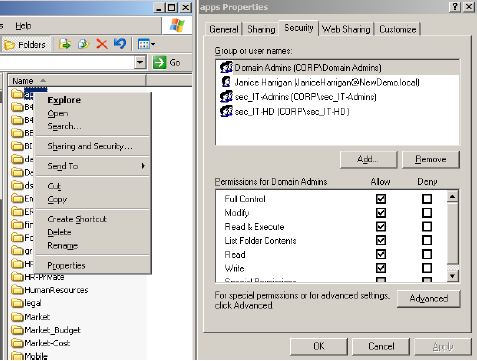
Now that we are aware of a few idiosyncrasies, let’s see if we can figure out who has access to a folder. In Windows, the first step in is to right-click on a folder, select properties, and then select the security tab:
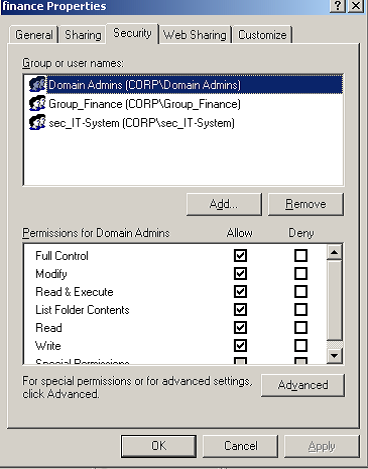
Listed in the top window of the security tab are the groups that have access to the folder, along with any explicitly named users (as opposed to users which are contained in groups). This list of groups and users is referred to as an Access Control List, or ACL; the groups and users listed are referred to as Access Control Entries, or ACE’s. Each ACE has a list of actions, or permissions, that it may perform on the folder, as listed in the lower window. We can see that the Domain Admins group has ‘Full Control’ on this folder. If we click on the other two groups, we will see their permissions, as well.
Unfortunately, our work is not yet complete. In order to properly ascertain who has access to each folder, we must determine who belongs to each group listed on the folder:
- Domain Admins
- Group Finance
- Sec_IT-System
In order to do that we’ll need to consult Active Directory, the directory service that stores these groups and their members. This ACL might have contained entries from the server’s local user and group repository as well—we got lucky on this one.
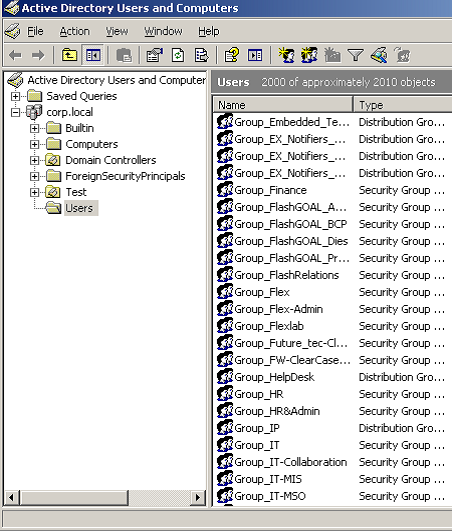
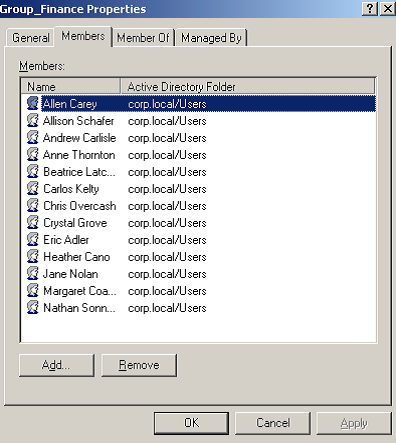
In the Active Directory Users & Computers MMC, we can double-click ‘Group Finance’, and look at the members tab to see the individual users.
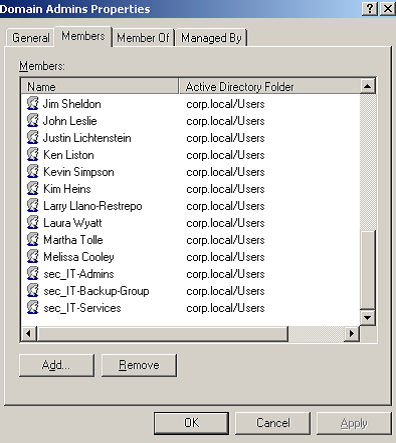
So we write these names down. Next, let’s check Domain Admins:
Again, we record all the names. At the bottom of this list, however, we notice that there are groups listed within the Domain Admins Group—these are referred to as nested groups. We’ll need to list all the members of these groups (and any nested groups), too. As you can see, answering what seems like a simple question—“Who has access to the finance folder?” can take quite a while.
Comedy is easy. Figuring out access is hard.
If you’re ever tasked with figuring out what someone has access to, it can also be time consuming. You’ll have to see if every folder must be examined to see if it contains the user or group in question, or if contains a group that the user or group in question is a member of.
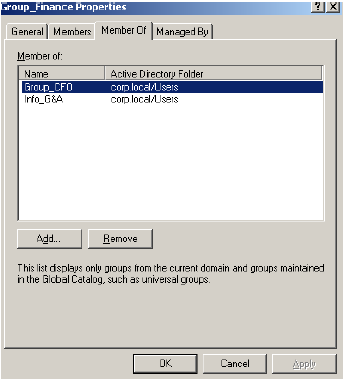
So first, we’ll have to look in Active Directory to see if Group_Finance is a member of any other groups:
Next, we’ll start right-clicking—any of those groups here?
How about the subfolders?
By the way, a terabyte of data contains roughly 50,000 folders, so this may take a while.
To fully grasp the enormity of this undertaking, consider that an enterprise will typically have tens or even hundreds of thousands of directories on each file server, while large file servers can contain a million or more directories each. It can take hours or even days to come up with an accurate list of the users who have access to a single directory and the process must be repeated for every directory. With constant changes in user roles and new user additions, along with growing data, by the time you think you’ve figured out who has access to what, it is likely to be obsolete.
Making decisions
Auditing
For administrators to make decisions about what to do with their organization’s data, they need to be able to quickly answer questions about the data. As we’ve seen in the examples above, answering questions – such as what someone has access to – might take longer than one would like. Even with the available tools, getting answers about our data is inadequate. The Windows Event View is unable to provide the level of detail needed. File System access logs provide too much data, get cumbersome quickly and slow servers down. Analytics and configuration management products deliver some relief in parsing logs, but you still end up spending hours trying to answer simple questions about activity and access settings. These tools give you a better way to search for the answers, but not the answers themselves. In the end, you need lots of time to use these tools, as well as a pair of expert eyes.
Data Ownership
Data owners need to be identified for more than just auditing: they need to be identified when data needs to be moved, archived, or when access permissions need to be modified. Using current methods, it’s very difficult to identify the business owners of unstructured data without a significant amount of effort. One way is to review the Access Control List (ACL) and contact every user listed. Alternatively, IT could examine the contents of the files within a directory and try to guess who the owner might be. Not only are these procedures extremely time-consuming and an inefficient use of IT time, they pose a security risk at the least and violate regulatory compliance at the most.
Change is hard
On any given day, a single folder may be accessible by 3-5 groups each containing 10-20 members with some overlap between each group. The folder may contain dozens of subfolders and thousands of files, many containing sensitive data. Over a single month, dozens of users in these groups will access thousands of files, usually several times a day. Content will be created, deleted, and changed. Permissions and group memberships will change.
If an administrator asks “If I had removed access for a single group of users on this container several months ago, who would have lost access, and what actual activity would have been affected by this change?”, the number of relationships required to answer these two questions for a single folder can exceed 100,000 – in a single month of activity. These relationships accumulate relentlessly in today’s environments.
In future environments, new data will be created, new servers will be added, new platforms will be created, and other types of metadata will eventually be desirable to collect and analyze, further increasing the number of functional relationships. The magnitude of the present and future data sets represent a formidable computing challenge – one that needed to be solved using standard computing infrastructure components, as specialized hardware would make any solution unfeasible.
So what’s an admin to do?
In order to meet this computing challenge, it would require a robust framework – namely the Varonis Metadata Framework – to collect, process, analyze and present metadata to IT and data owners that could scale to present and future requirements. With this framework, you’ll be able to ensure that the right people will have access to only the data that they need to perform their jobs. You will automatically improve security, reduce risk, and take a significant step toward least-privilege access compliance.
Sign-up for a 1-on-1 demo of Varonis DatAdvantage to see how we do it!
What you should do now
Below are three ways we can help you begin your journey to reducing data risk at your company:
- Schedule a demo session with us, where we can show you around, answer your questions, and help you see if Varonis is right for you.
- Download our free report and learn the risks associated with SaaS data exposure.
- Share this blog post with someone you know who'd enjoy reading it. Share it with them via email, LinkedIn, Reddit, or Facebook.